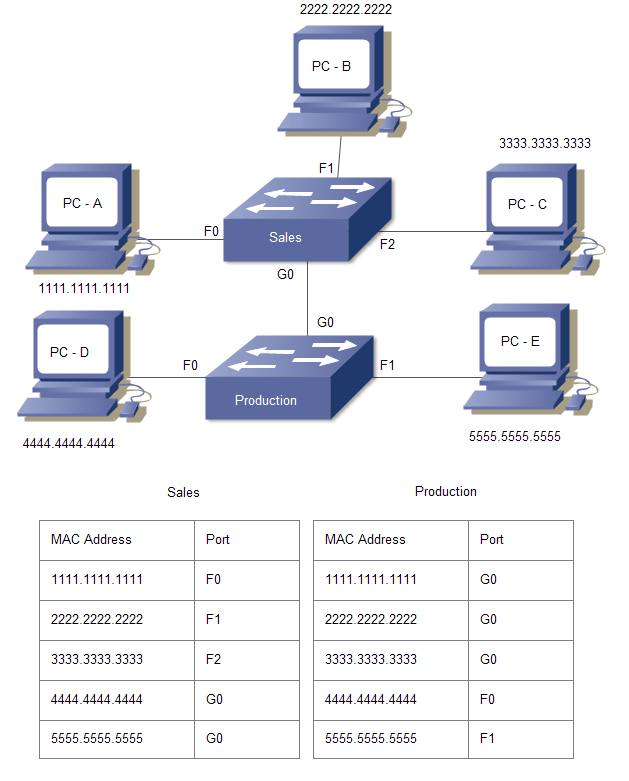
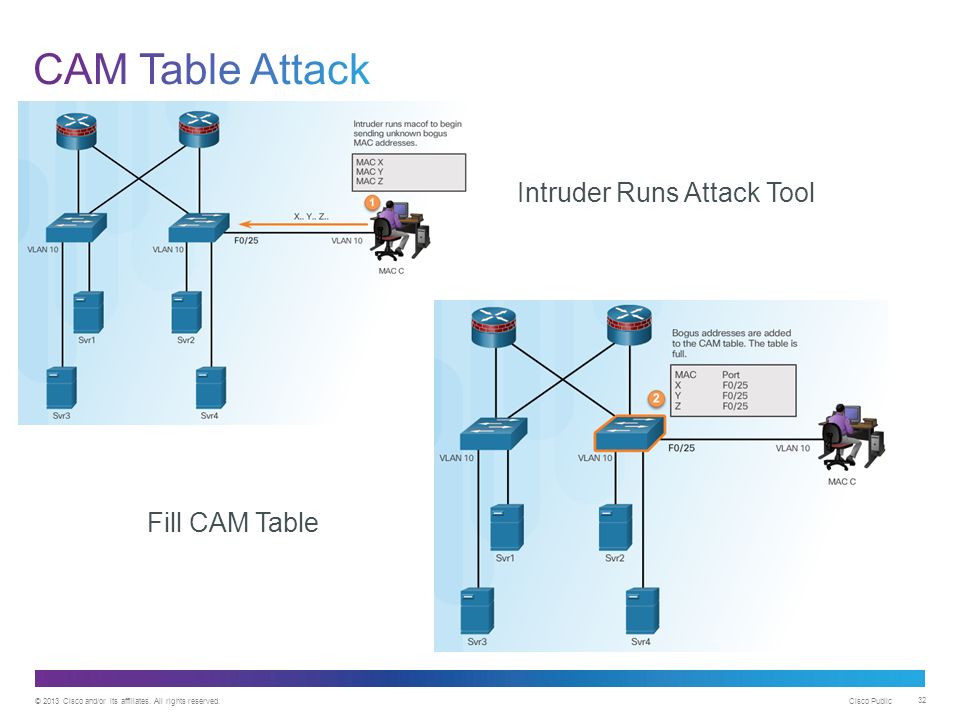
![PDF] Switch's CAM table poisoning attack: hands-on lab exercises for network security education | Semantic Scholar PDF] Switch's CAM table poisoning attack: hands-on lab exercises for network security education | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9b543909f9357003dbab20e87f210f5893d61bb5/2-Figure1-1.png)
PDF] Switch's CAM table poisoning attack: hands-on lab exercises for network security education | Semantic Scholar

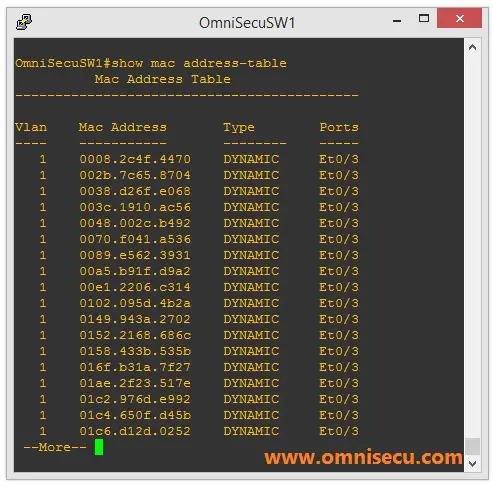
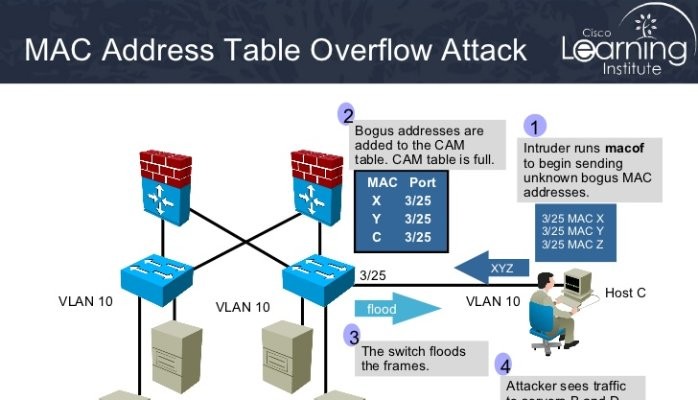
2007 Cisco Systems, Inc. All rights reserved.ISCW-Mod9_L8 1 Network Security 2 Module 7 – Secure Network Architecture and Management. - ppt download




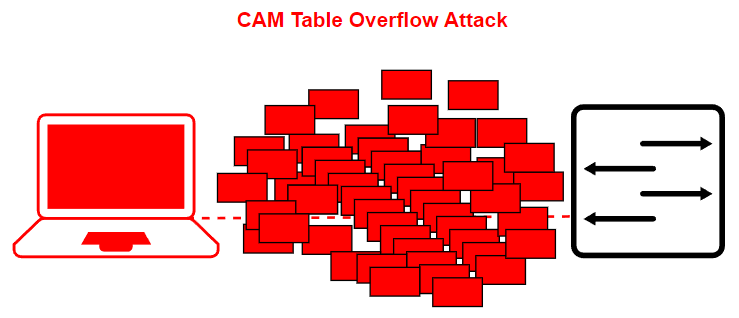
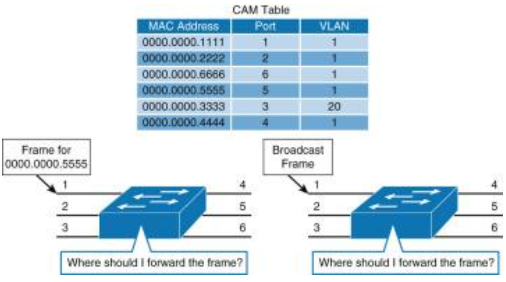
![How the switch uses the CAM tables - Python Penetration Testing Essentials [Book] How the switch uses the CAM tables - Python Penetration Testing Essentials [Book]](https://www.oreilly.com/api/v2/epubs/9781789138962/files/assets/4f76d848-e99f-42e0-b0e0-38b7d139b0df.png)